Single Sign-On for Google Apps
UML Activity Diagram Example
An example of UML activity diagram describing Single Sign-On (SSO) to Google Apps.
To interact with partner companies Google uses single sign-on based on OASIS SAML 2.0 protocol. Google acts as service provider with services such as Gmail or Start Pages. Partner companies act as identity providers and control user names, passwords, and other information used to identify, authenticate and authorize users for web applications that Google hosts. Each partner provides Google with the URL of its SSO service as well as the public key that Google will use to verify SAML responses.
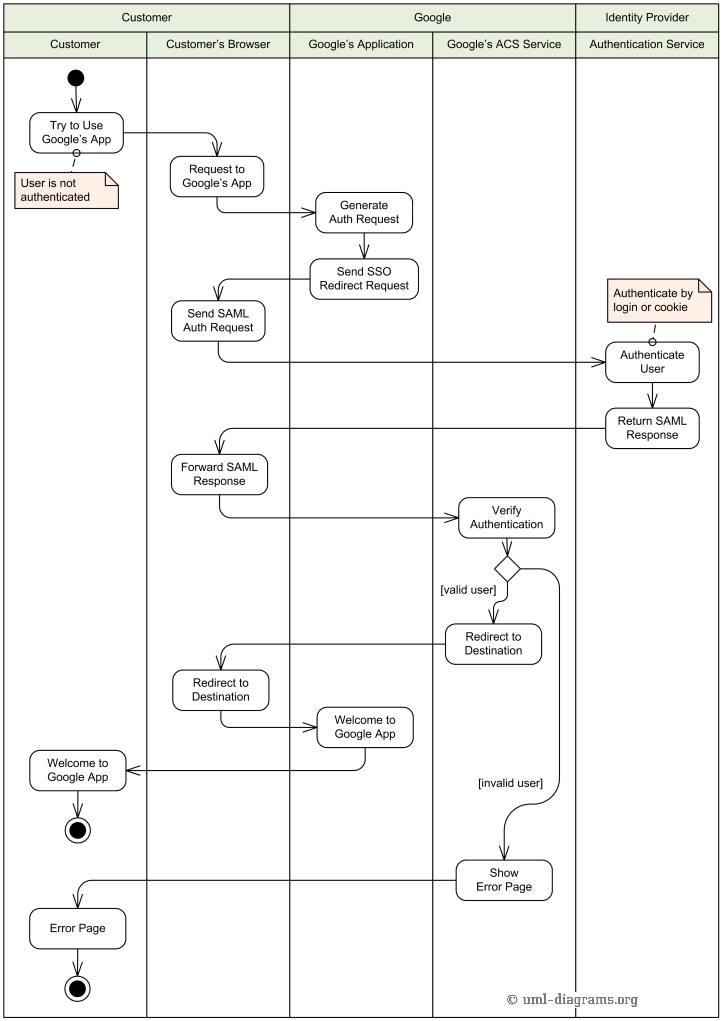
An example of UML activity diagram for Single Sign-On to Google Apps.
When a user attempts to use some hosted Google application, such as Gmail, Google generates a SAML authentication request and sends redirect request back to the user's browser. Redirect points to the specific identity provider. SAML authentication request contains the encoded URL of the Google application that the user is trying to reach.
The partner identity provider authenticates the user by either asking for valid login credentials or by checking for its own valid authentication cookies. The partner generates a SAML response and digitally signs it. The response is forwarded to Google's Assertion Consumer Service (ACS).
Google's ACS verifies the SAML response using the partner's public key. If the response is valid and user identity was confirmed by identity provider, ACS redirects the user to the destination URL. Otherwise user will see error message.